Right after introducing the first Windows Server 2012 R2 domain controller in Windows Server 2003 network, besides changes in DHCP server and transferring FSMO roles
the first Windows Server 2012 R2 domain controller in Windows Server 2003 network, besides changes in DHCP server and transferring FSMO roles , it is also important to review and set correct values for DNS server addresses on both domain controllers. DNS is integral part of Active Directory Domain Services, therefore the proper functioning of the entire domain practically depends on proper functioning of the DNS servers.
, it is also important to review and set correct values for DNS server addresses on both domain controllers. DNS is integral part of Active Directory Domain Services, therefore the proper functioning of the entire domain practically depends on proper functioning of the DNS servers.
What you will read in this post:
1. DNS settings of a single domain controller in Active Directory Site
2. Configure DNS server addresses on multiple Domain Controllers in Active Directory Site
3. General recommendations for configuring DNS on Domain Controllers
4. Configure DNS Forwarders on Domain Controller
Let’s begin.
1. DNS settings of a single Domain Controller in Active Directory Site
In my case, here is what I had for DNS on my Windows Server 2003 DC before introducing Windows Server 2012 R2:
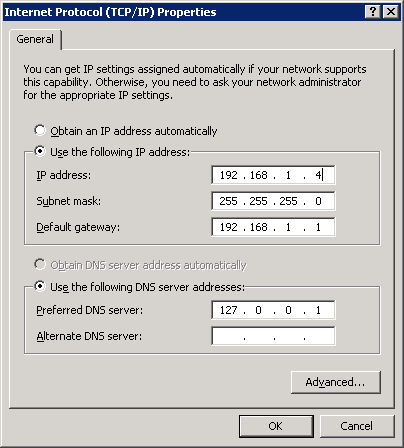
Since it was the only one DNS server in the domain, it was using its loopback IP address as preferred DNS server. There were no issues for resolving names within the domain itself, and for resolving external names I have had public DNS servers configured in DNS Forwarders. As I mentioned before, all DC and DNS tests were positive.
2. Configure DNS server addresses on multiple Domain Controllers in Active Directory Site
As I wrote in the post “Introducing Windows Server 2012 as second domain controller ” – before installing Active Directory Domain Services and DNS on the Windows Server 2012 R2 (in this case study I call it also “Server D”), as DNS server for Server D was set the IP address of the Windows Server 2003 (as only one DNS in the domain, logically). However, after the successful promotion of Server D as domain controller, here is what have changed automatically:
” – before installing Active Directory Domain Services and DNS on the Windows Server 2012 R2 (in this case study I call it also “Server D”), as DNS server for Server D was set the IP address of the Windows Server 2003 (as only one DNS in the domain, logically). However, after the successful promotion of Server D as domain controller, here is what have changed automatically:
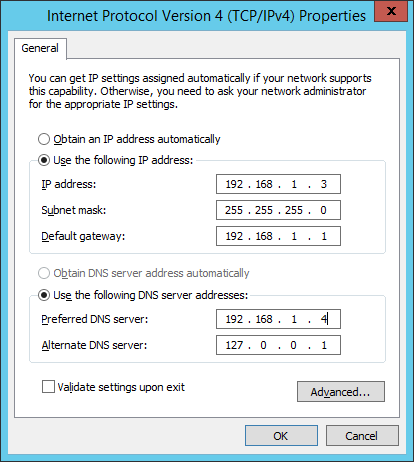
The value for Preferred DNS server remained the same (the IP address of the Windows Server 2003), but as Alternate DNS server was set the loopback IP address of the newly promoted domain controller (Windows Server 2012 R2) i.e. the configuration wizard has automatically configured the DNS settings according to the general recommendations from Microsoft.
3. General recommendations for configuring DNS on Domain Controllers
When I say general recommendations from Microsoft, I mean on general guidelines that Microsoft AD and Networking Support teams give to customers. Check this page on Ask the Directory Services Team
on Ask the Directory Services Team blog and especially the question “What is Microsoft’s best practice for where and how many DNS servers exist? What about for configuring DNS client settings on DC’s and members?“. I hope you will find your answers.
blog and especially the question “What is Microsoft’s best practice for where and how many DNS servers exist? What about for configuring DNS client settings on DC’s and members?“. I hope you will find your answers.
There are many discussions what should be set as first and what as second DNS
what should be set as first and what as second DNS , especially when your DC’s are in different Active Directory sites.
, especially when your DC’s are in different Active Directory sites.
However, for a single site with more than one domain controller, things seem to be relatively simple:
- on each DC, always put the other DNS as its primary DNS server
- each DC should include the loopback address 127.0.0.1 in the list of DNS servers, but not as first entry.
If you have more complex environment then consider this extensive library with resources as starting point for everything regarding Domain Name System.
with resources as starting point for everything regarding Domain Name System.
Let’s get back to the story.
Having this logic in mind and following the above mentioned guidelines, I had to change the original DNS settings on the Windows Server 2003 (Server A) since now we have different situation. On the NIC adapter on Server A, I set the Server D as primary DNS server and its loopback IP address 127.0.0.1 as secondary DNS.
4. Configure DNS Forwarders on Domain Controller
What I have done until now:
- set correct DNS settings on Server A after promotion of Server D – checked;
- set correct DNS settings on Server D – checked (configured automatically during the configuration wizard);
- configure DNS Forwarders on Server A – checked (previously configured);
- configure DNS Forwarders on Server D – missing.
Although everything worked normally and all DNS requests have being resolved quickly, a single point of failure was existing because only Server A have DNS forwarders configured. This means if Server A goes down, communication chain to the public DNS servers is broken and resolving the names outside of the domain will become impossible. This is additionally confirmed in the results of the Best Practices Analyzer for the DNS role in Server D (Windows Server 2012 R2).
for the DNS role in Server D (Windows Server 2012 R2).
Contrary to Windows Server 2003, in Windows Server 2012 R2 when you configure DNS forwarders the system automatically tries to resolve their IP addresses into their FQDN and vice versa:
DNS forwarders the system automatically tries to resolve their IP addresses into their FQDN and vice versa:
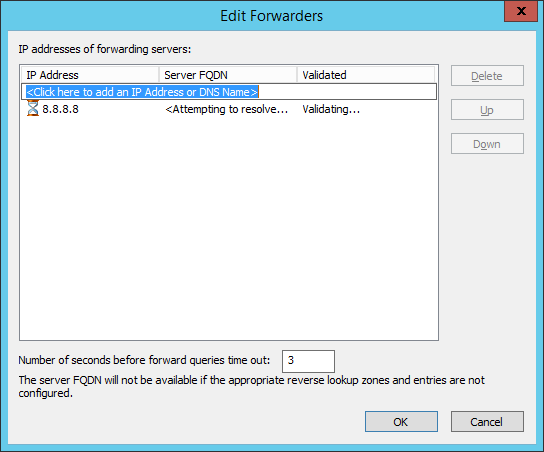
However, a problem with external name resolution appeared. The DNS server was not able to resolve the IP 8.8.8.8 (one of Google’s public DNS servers) into FQDN:
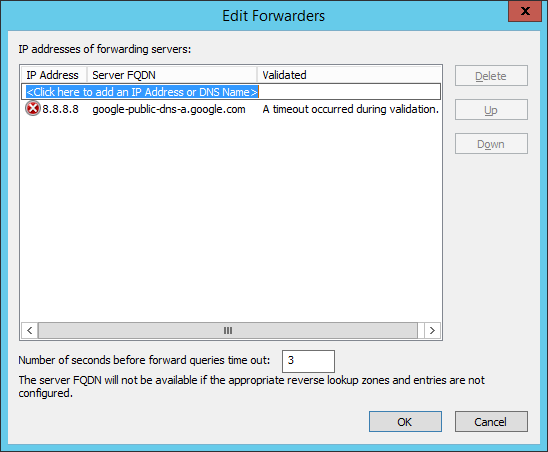
I open command prompt and tried with nslookup command, also without success:
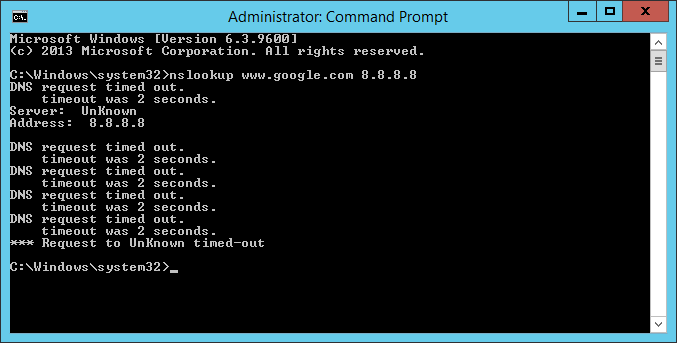
It turned out that the corporate firewall was blocking this DNS requests from Server D (where I was trying to configure DNS Forwarders) to the external world. After modifying the DNS rule in the firewall, everything was back to the normal:
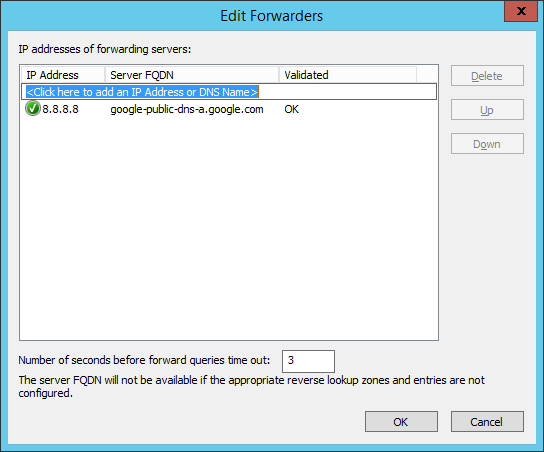
And nslookup command as well:
Well, now we have both servers with properly configured settings for internal DNS resolution as well as for external resolution.
Running a full dcdiag test at the end, also confirmed the correct DNS configuration of both servers for the domain.
The results after running Best Practices Analyzer have showed a warning “DNS: The DNS Server should have scavenging enabled” which is a “mechanism for performing cleanup and removal of stale resource records, which can accumulate in zone data over time”. Read more about Aging and Scavenging
“DNS: The DNS Server should have scavenging enabled” which is a “mechanism for performing cleanup and removal of stale resource records, which can accumulate in zone data over time”. Read more about Aging and Scavenging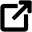 .
.
After configuring the Scavenging on Server D (with default value of 7 days), everything was fine with BPA results. I didn’t configure scavenging on Server A simply because it was working fine and moreover it is going to be demoted soon.
Finally, the DNS part is over.


Hi Milan Mihajlov,
Nice Post
thanks For guide about DNs settings it is very helpful .
This post has been a life save!!! i have been scratching my head for days knowing I have a niggling DNS problem somewhere after adding my first 2012 R2 DC to a 2003 domain with a single DC…. should have known it would be something so stupidly simple (setting the preffered DNS server address on the old DC to the new DC and loopback address for the second one!!)
Thanks for a great post!!!
Thanks Jon! If you have any other issue that could convert into a good article, let me know.
Great article Milan!
I ran into a strange forwarder configuration the other day – need your oppinion:
2 DCs working as DNS:
DC1 has external forwarders like Googles 8.8.8.8
DC2 has DC1 as forwarder!
I do not see any sense in that – completely faulty configuration!
Hi Mike. Did you try to configure DNS settings as it was explained in the article or you kept the mentioned configuration with DC1 configured as forwarder for DC2? Another thing, did you review the Event Viewer logs, especially the DNS logs? What do they say?
Hi Milan,
Great post! Thanks.
I am running 2 DCs, and wondering on setting up forwarders for my domain controllers. I am using opendns ip address as external forwarders, and setup all the workstations for automatically get DNS server address. It works fine, except the workstations can’t access the network files. When I changed the DNS server address on the workstation to point to the 2 domain controllers ip addresses, it works great. My question is, what setting should I use for forwarders on my domain controller, so I can keep the setting on the workstations to get DNS address automatically?
Thanks!
Hello Tan. I apologize for replying a bit later. In my opinion, if I understood your question well, you should configure your internal DHCP server to assign the IP addresses of your DC’s as DNS setting on all workstations, and on the other side configure external forwarders on your DNS servers (the 2 DC’s) with IP addresses of OpenDNS. Because, in your case the workstations couldn’t resolve internal network resources because they were pointing outside of your network (OpenDNS).
You shouldn’t use the loopback address 127.0.0.1 on your DC’s network settings. This is the old way. Since Windows 2012 you should use the private IP of the DC here. I know there is a lot of discussion about this point but round about 80% of all administrators agree with this opinion.
Thanks Tobi for your feedback. It would be nice if you could provide a good resource where this statement is well explained, that will be very beneficial for our readers.
Of course.
http://firelogic.net/best-practices-for-windows-server-dns-and-how-to-avoid-the-common-pitfalls/
http://www.itnotes.eu/?p=3126
Bit late on the reply, but in my defence I’ve only just had reason to scour through all the docs available on DNS and the loopback argument.
The link Tobi provided only mentions this shouldn’t be done, but didn’t provide any reasons for not doing so: “modern Windows networks do not like to see this” doesn’t explain anything other than the authors opinion on the subject. Does anyone have anything else on the should v shouldn’t of loopback in DNS settings?
Officially from the vendor:
https://technet.microsoft.com/en-us/library/ff807362(WS.10).aspx
For me using loopback as a second DNS has been the way to go for the last 15 years. It is faster also…
Please confirm in order to perform external resolution using conditional forwarding method to google dns, 8.8.8.8. Does internet connectivity require to have in the DC system? Currently my domain is not having internet connectivity and are in secure sub net.
If I want to achieve, this, how I can do this? My all the request is being resolved internally. But our requirement is to resolve externally to one particular domain as it has a VPN tunnel dependency.
Hi, I apologize for replying later than usual. I assume you don’t want to connect your DC to internet but it would be hard to achieve DNS resolution without Internet link. Except if you consider to deploy something like “DNS relay”. In that case you may continue to use your DC without internet but it should be connected to the DNS relay. You will need an experienced network engineer to configure this solution, depending on your network settings.
Hi, Dear
Help me
I have installed and configured server 2012 R2 with kerio control as firewall
just MY WEBSITE (LIVE DOMAIN) DO NOT WORK , its message: “This site can’t be reached, www.MYDOMAIN.gov.af’s server DNS address could not be found.”
Hi. This problem description is way too general.
Thanks a lot for the article, this become handy for my problem.
Glad to help